Mobile app security is critical in today’s digital world – but how do you sharpen your skills without breaking the law? Intentionally vulnerable Android apps are the perfect solution. Designed for security enthusiasts, these apps simulate real-world flaws, letting you practice mobile application penetration testing legally and ethically.
Whether you’re a beginner or a seasoned pro, this guide covers the best purposefully insecure and vulnerable Android applications to build your skills. We’ve handpicked apps that mirror the OWASP Mobile Top 10 risks, CTF-style challenges, and hybrid app vulnerabilities. Let’s dive in!
Why Practice with Vulnerable Apps?
✅ Safe & Legal: Test exploits without harming real users.
✅ Realistic Scenarios: Mimic flaws like insecure data storage, hardcoded secrets, or broken cryptography.
✅ Skill Validation: Prep for certifications (ex. eMAPT certification) or bug bounties.
✅ Security-Compliant Learning: All apps are open-source, vetted by security communities like OWASP.
Pro Tip: Run these in an Android emulator (Genymotion or Android Studio) or a dedicated test device.
Table of Contents
The Ultimate List: Vulnerable Android Apps for Pentesting
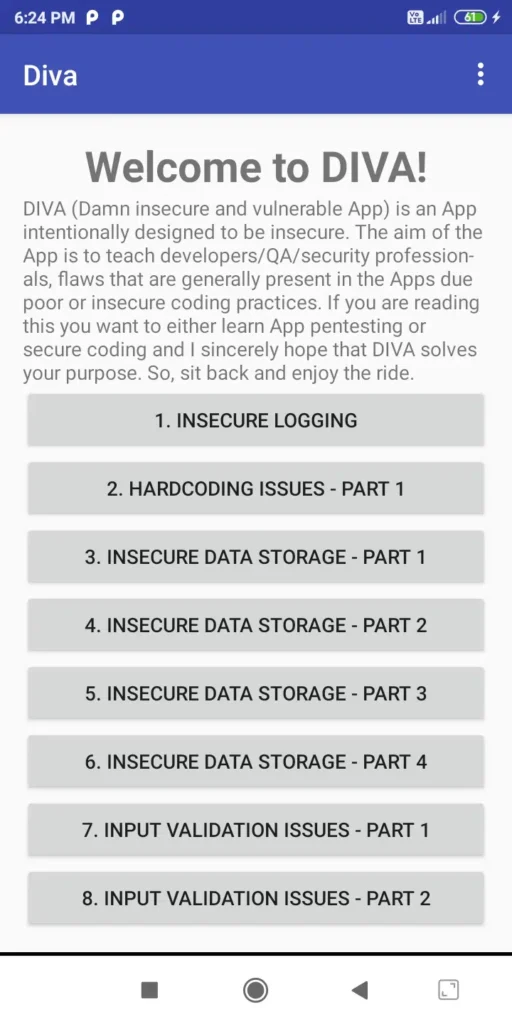
1. DIVA Android (Damn Insecure and vulnerable App for Android)
- Purpose: A “Damn Insecure and Vulnerable App” covering foundational flaws.
- Challenges:
- Insecure logging
- Hardcoded credentials
- Input validation bypass
- Access control flaws
- GitHub: Download DIVA
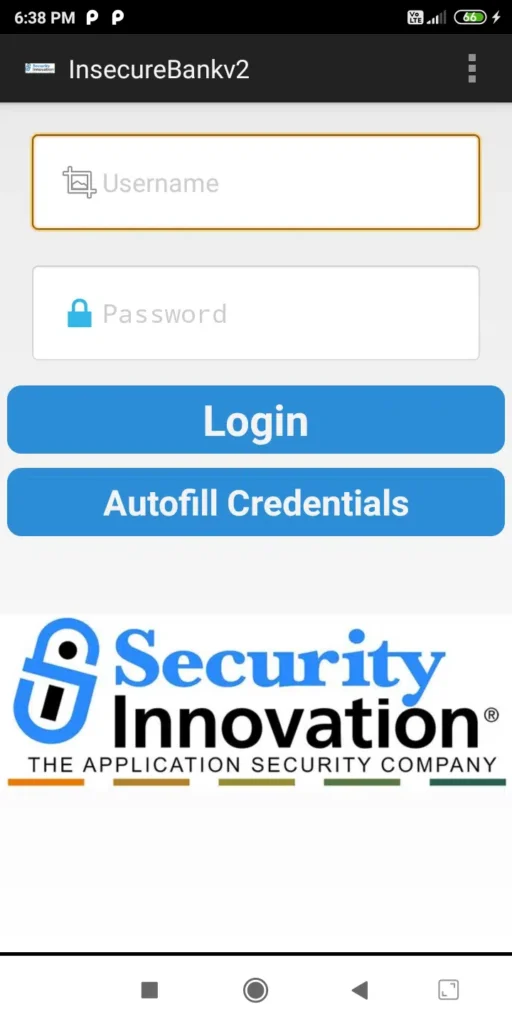
2. Android InsecureBank v2
On the Android InsecureBank v2 app, we can test for both static and dynamic types of vulnerabilities. We can configure its server on our local PC and connect it.
- Purpose: A banking app riddled with 20+ flaws – ideal for dynamic testing.
- Challenges:
- Flawed Broadcast Receivers
- Intent Sniffing and Injection
- Weak Authorization mechanism
- Local Encryption issues
- Vulnerable Activity Components
- Root Detection and Bypass
- Emulator Detection and Bypass
- Insecure Content Provider access
- Insecure Webview implementation
- Weak Cryptography implementation
- Application Patching
- Sensitive Information in Memory
- Insecure Logging mechanism
- Android Pasteboard vulnerability
- Application Debuggable
- Android keyboard cache issues
- Android Backup vulnerability
- Runtime Manipulation
- Insecure SDCard storage
- Insecure HTTP connections
- Parameter Manipulation
- Hardcoded secrets
- Username Enumeration issue
- Developer Backdoors
- Weak change password implementation
- GitHub: Get InsecureBank v2
3. hpAndro Android AppSec (Kotlin)
You can find the collection of the apps with different-different types of vulnerabilities on their Playstore directory and the CTF portal. It’s a very helpful open-source collection of vulnerable labs.
- Purpose: CTF-style challenges with live scoring.
- Challenges:
- HTTP Traffic
- Public Key Pinning
- Non-HTTP Traffic
- WebSocket Traffic
- Root Detection
- Emulator detection
- Anti-Debugging detection
- Insecure Data Storage
- Logs
- Content Providers
- Encryption
- Symmetric Encryption
- Asymmetric Encryption
- Hashing
- Authentication
- Binary Protection
- Device ID
- Web Application
- Miscellaneous
- Play Store & CTF Portal: hpAndro Apps | CTF Platform
- Walkthrough: https://www.youtube.com/c/AndroidAppSec
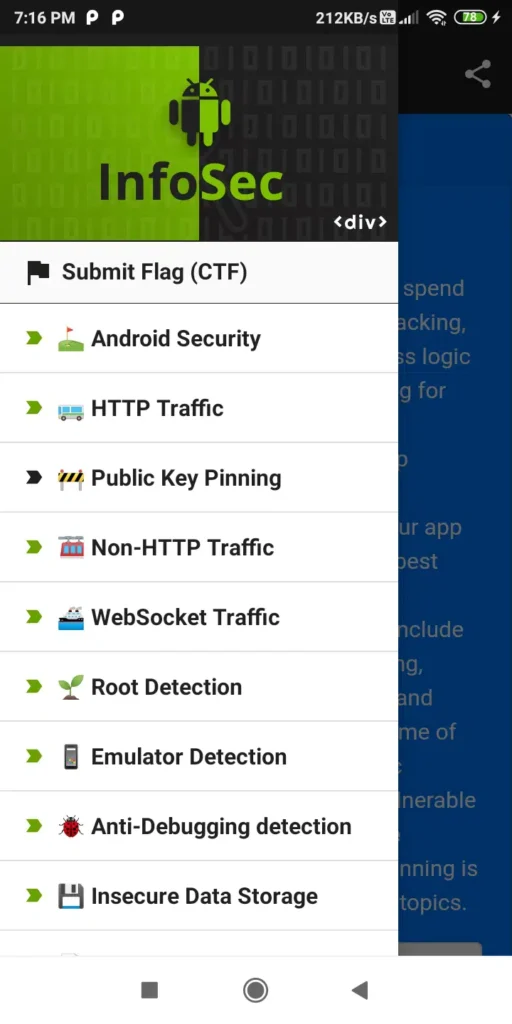
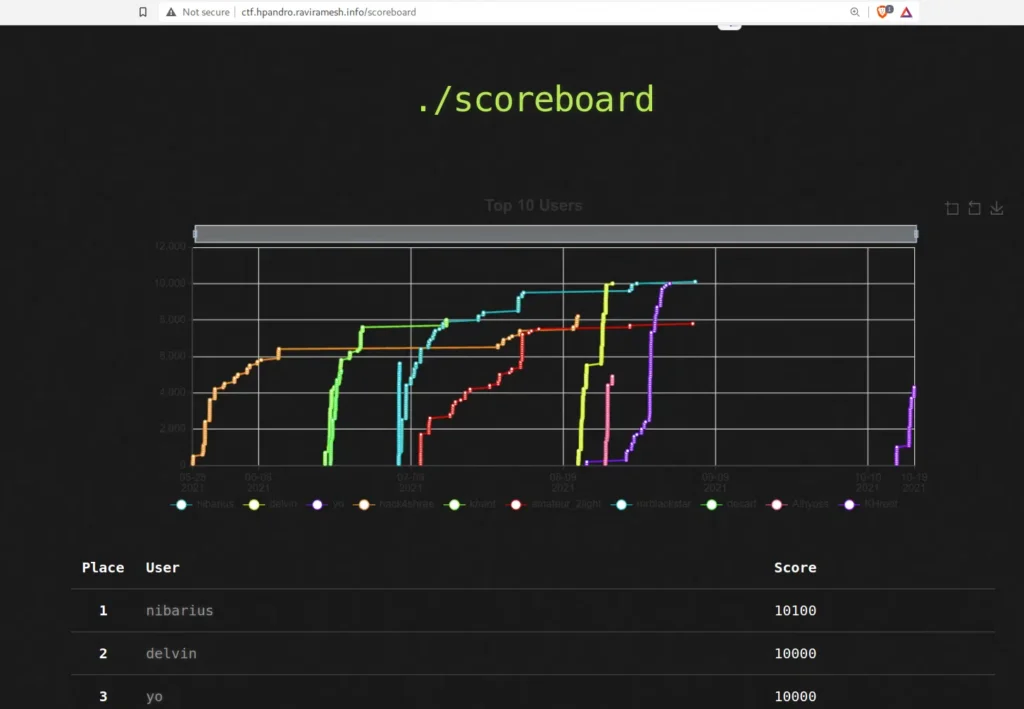
CTF Dashboard:
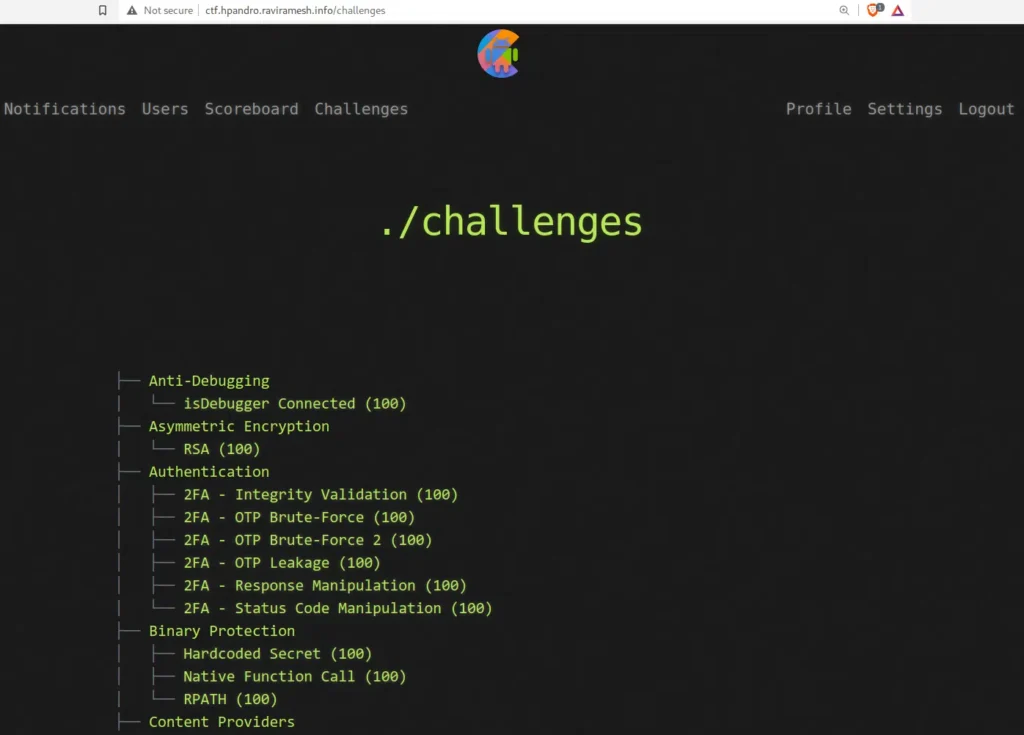
CTF Scoreboard:
4. MSTG Hacking Playground
Mobile Security Testing Guide(MSTG) Hacking Playground has available for both android and iOS.
- Purpose: Official OWASP lab for testing Mobile Security Testing Guide (MSTG) techniques.
- Challenges:
- Secure coding anti-patterns
- Reverse engineering tasks
- URL: https://github.com/OWASP/MSTG-Hacking-Playground
- GitHub: Java | Kotlin
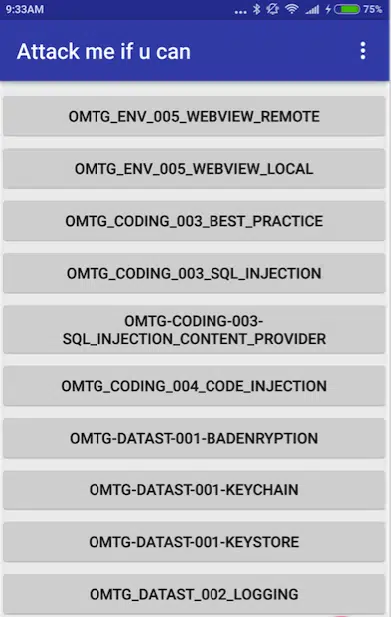
5. InjuredAndroid
InjuredAndroid is a CTF-styled vulnerable android application.
- Purpose: A fun CTF with flags for common vulnerabilities.
- Challenges:
- Exported activity exploits
- Deep link manipulation
- GitHub: Download Here

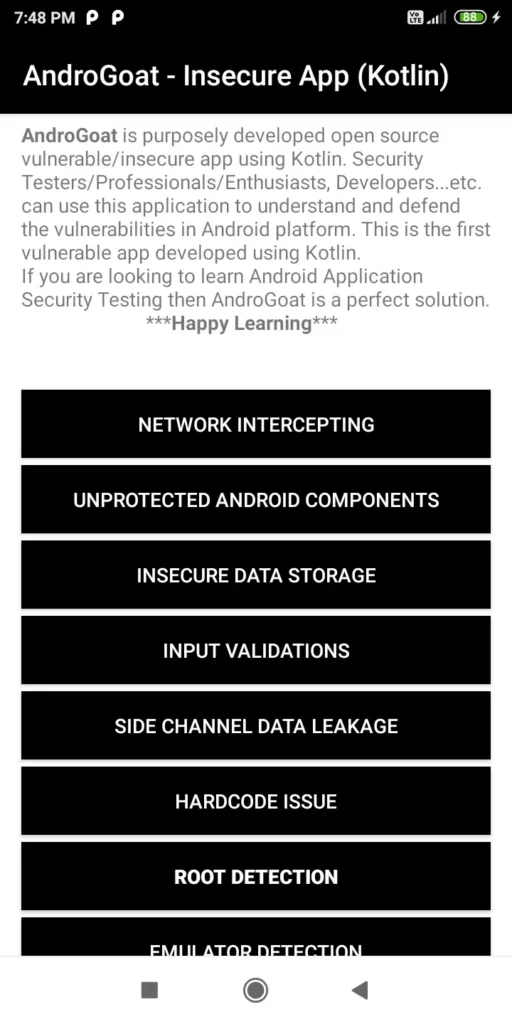
6. AndroGoat
AndroGoat is purposely developed open source vulnerable/insecure app using Kotlin.
- Purpose: Kotlin-based app with guided walkthroughs.
- Challenges:
- Root Detection
- Emulator Detection
- Insecure Data Storage – Shared Prefs – 1
- Insecure Data Storage – Shared Prefs – 2
- Insecure Data Storage – SQLite
- Insecure Data Storage – Temp Files
- Insecure Data Storage – SD Card
- Keyboard Cache
- Insecure Logging
- Input Validations – XSS
- Input Validations – SQLi
- Input Validations – WebView
- Unprotected Android Components – Activity
- Unprotected Android Components –Service
- Unprotected Android Components – Broadcast Receivers
- Hard coding issues
- Network intercepting – HTTP
- Network intercepting – HTTPS
- Network intercepting – Certificate Pinning
- Misconfigured Network_Security_Config.xml
- Android Debuggable
- Android allowBackup
- Custom URL Scheme
- Broken Cryptography
- Walkthroughs: AndroGoat Tutorials
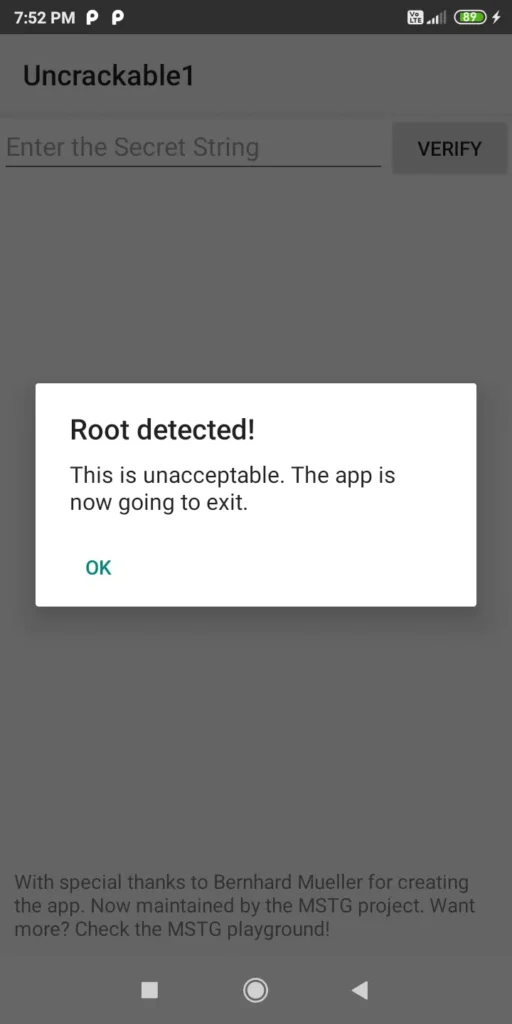
7. OWASP Crackmes
A set of apps for Android and iOS to test your Android application hacking skills.
- Purpose: Reverse engineering challenges from OWASP’s MSTG.
- Skills Tested:
- APK decompilation
- Runtime manipulation
- GitHub: Crackmes Collection
8. Sieve App
- Purpose: A password manager with critical flaws.
- Challenges:
- SQL injection
- Directory traversal
- Insecure Content Provider access
- Authention bypass
- Data leakage
- Exploit Guide: SievePWN
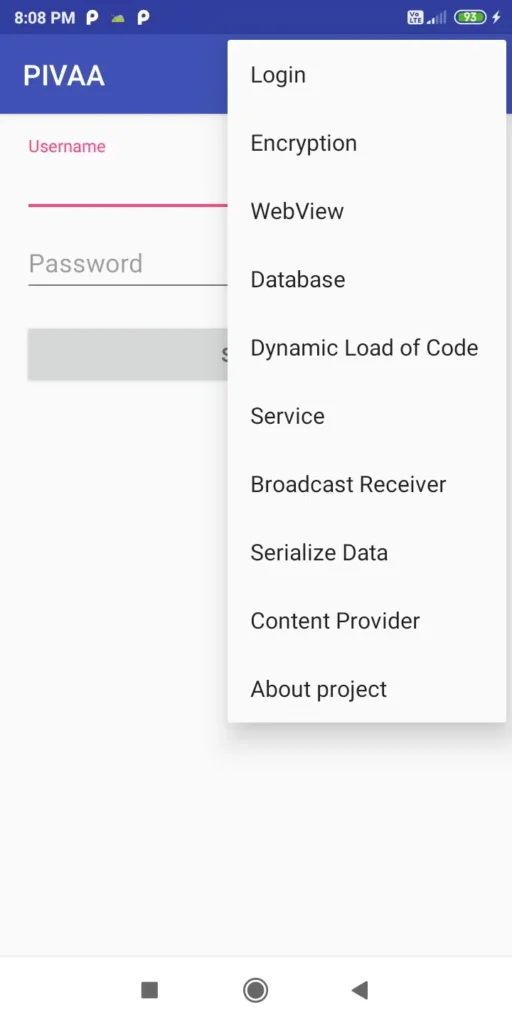
9. Purposefully Insecure and Vulnerable Android Application(PIIVA)
- Purpose: Covers 20+ vulnerabilities in one app.
- Highlights:
- Usage of weak Initialization Vector
- Man-In-The-Middle Attack
- Remote URL load in WebView
- Object deserialization
- SQL injection
- Missing tapjacking protection
- Enabled Application Backup
- Enabled Debug Mode
- Weak encryptionvHardcoded encryption keys
- Dynamic load of codevCreation of world readable or writable files
- Usage of unencrypted HTTP protocol
- Weak hashing algorithms
- Predictable Random Number Generator
- Exported Content Providers with insufficient protection
- Exported Broadcast Receivers
- Exported ServicesvJS enabled in a WebView
- Deprecated setPluginState in WebView
- Hardcoded data
- Untrusted CA acceptance
- Usage of banned API functions
- Self-signed CA enabled in WebView
- Path Traversal
- Cleartext SQLite database
- Temporary file creation
- GitHub: PIIVA Project
10. Damn Vulnerable Hybrid Mobile App (DVHMA)
- Purpose: Targets hybrid apps (WebView + native code).
- Challenges:
- JavaScript bridge exploits
- Cordova plugin misconfigs
- GitHub: DVHMA

11. Damn Vulnerable Bank
- Purpose: Simulates banking app threats (e.g., credential stuffing).
- Challenges:
- Session hijacking
- API parameter tampering
- GitHub: Download Damn Vulnerable Bank app
How to Set Up Your Lab
- Tools You’ll Need:
- Emulator: Genymotion or Android Studio.
- Analysis Tools: MobSF, Frida, Burp Suite.
- Decompilers: jadx-gui, APKTool.
- Pro Tips:
- Isolate apps in a virtual network.
- Root your test device for advanced testing (use Magisk).
Final Thoughts
Practicing on vulnerable Android applications for penetration testing is the fastest way to master mobile security. These apps turn theory into muscle memory – whether you’re bypassing root detection or exploiting WebViews. Remember: Always test ethically!
Explore More:







