Let me tell you about one of the most useful tools you’ll ever use in penetration testing – SearchSploit. If you’ve ever spent hours manually browsing through exploit databases looking for that perfect vulnerability, you’ll understand why this tool is absolutely game-changing.
SearchSploit is basically your personal assistant for finding exploits. It’s a command-line tool that searches through the massive Exploit Database offline, which means you can hunt for exploits even when you’re stuck without internet access during a penetration test.
Understanding SearchSploit Fundamentals
Think of SearchSploit as having a conversation with the world’s largest exploit library. The searchsploit tool was created by Offensive Security, and it’s become the go-to solution for security professionals who need quick access to thousands of exploits, shellcodes, and proof-of-concept codes.
What makes this tool special isn’t just its size – it’s the speed and convenience. You can search by software names, version numbers, CVE identifiers, or even specific vulnerability types. The best part? Everything happens locally on your machine, so you’re not dependent on internet connectivity.
The tool comes pre-installed on Kali Linux, but don’t worry if you’re using something else. Getting searchsploit running on Ubuntu, Debian, Arch Linux, or even macOS is pretty straightforward. There’s even a Docker version available if that’s more your style.
Table of Contents
SearchSploit Installation Methods
Kali Linux Setup
If you’re already using Kali Linux, you’re in luck – SearchSploit is ready to go. But let’s make sure everything’s updated:
sudo apt update && sudo apt install exploitdb searchsploit -u
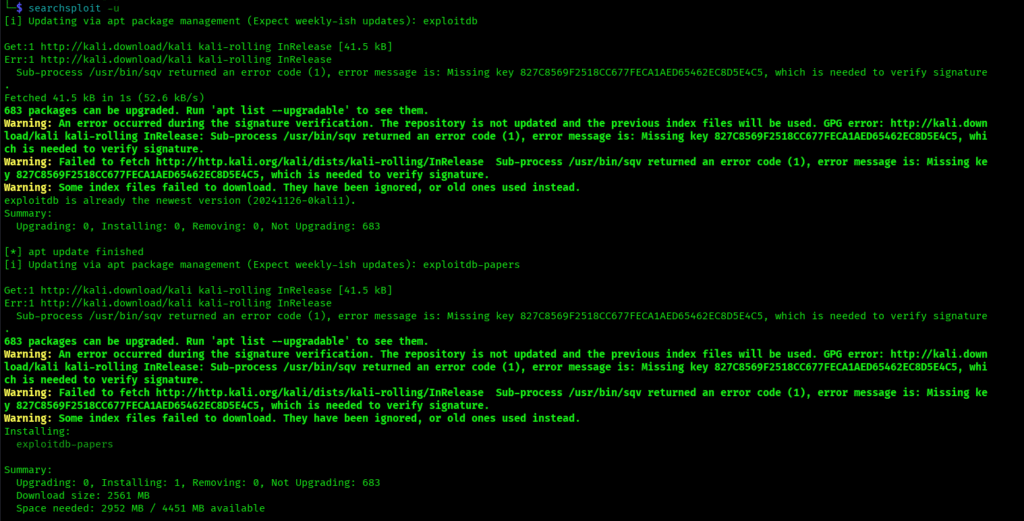
That update command is crucial because new exploits are added regularly, and you want access to the latest discoveries.
Ubuntu/Debian Installation Process
Getting searchsploit install ubuntu working is straightforward. You’ll want to install the complete package:
sudo apt update sudo apt install exploitdb exploitdb-bin-sploits exploitdb-papers
This gives you everything – the main exploit database, binary exploits, and research papers. It’s like getting the complete security research library.
Arch Linux Installation
For Arch users, searchsploit arch installation is available through the AUR:
yay -S exploitdb
Alternative Installation Methods
Don’t like package managers? No problem. You can grab SearchSploit directly from the searchsploit github repository, which often has the newest features before they hit official packages. There’s also a Docker container available, and you can even compile from source if needed.
Core Command Options: A SearchSploit Cheat Sheet
Let me walk you through the essential commands that’ll make you productive with SearchSploit. Each option serves a specific purpose, and understanding them will dramatically improve your exploit hunting efficiency.
Basic Search Commands
Search by Service or Software
This is your starting point. Just type what you’re looking for:
# searchsploit [search_term]
searchsploit apache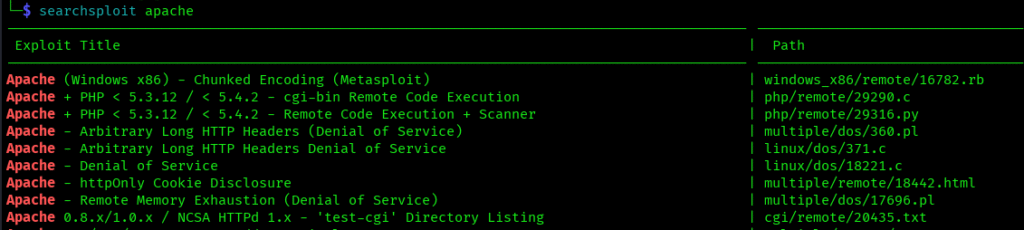
Search by Title keywords (-t, –title)
This option restricts your search to exploit titles only, which is incredibly useful when you want precise results:
searchsploit -t apache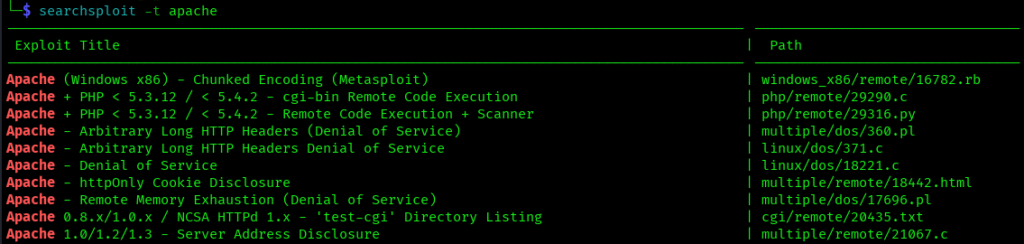
Use this when you’re getting too many results and want to focus on exploits that specifically mention your target in the title.
-e, –exact
Forces an exact match for your search term:
searchsploit -e "apache 2.4"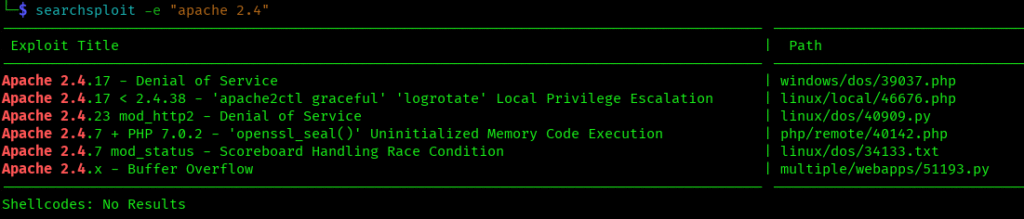
Perfect when you know the exact software version and don’t want partial matches cluttering your results.
-s, –strict
Enables strict search mode for more precise matching:
searchsploit -s apacheThis tightens up the search algorithm to reduce false positives.
-c, –case
Makes your search case-sensitive:
searchsploit --case Apache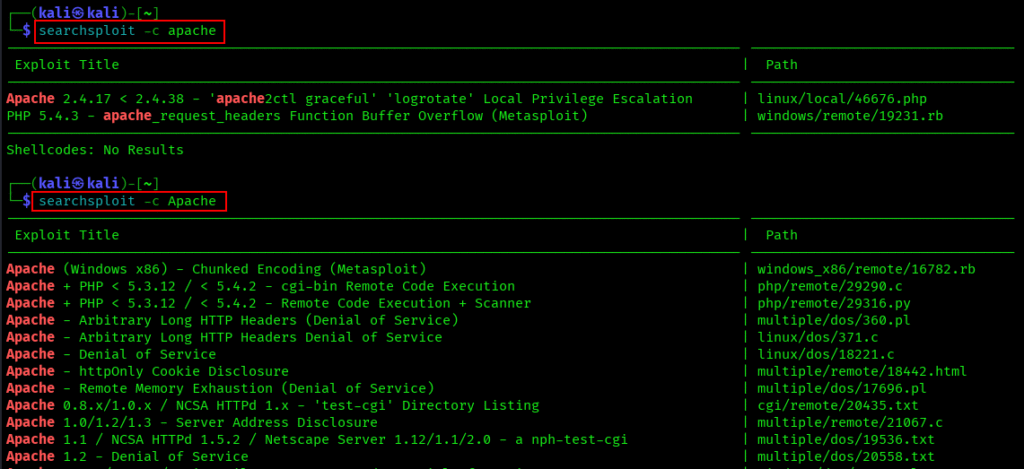
Useful when dealing with software that has specific capitalization requirements.
Information Display Options
-w, –www
Shows web URLs where you can view the exploits online:
searchsploit -w apache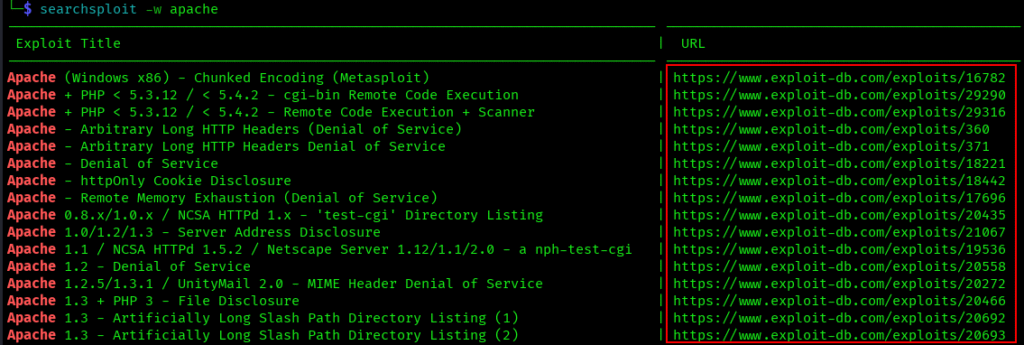
Great for quickly sharing exploit links with team members or bookmarking interesting finds.
Search by CVE (–cve)
Displays CVE numbers associated with exploits:
searchsploit --cve 2021-41773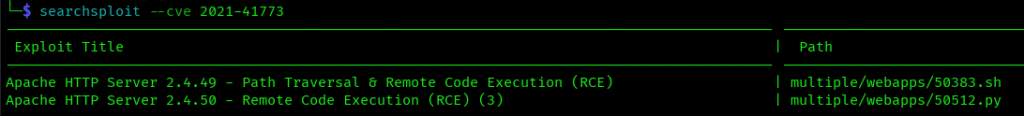
Essential for cross-referencing with vulnerability reports and compliance documentation.
-v, –verbose
Provides detailed output with additional information:
searchsploit -v apacheShows more context about each exploit, including file paths and additional metadata.
–id [EDB-ID]
Searches for a specific exploit by its database ID:
searchsploit --id 12345
Use this when you have a specific EDB-ID from a report or reference.
-j, –json
Outputs results in JSON format for scripting:
searchsploit -j apache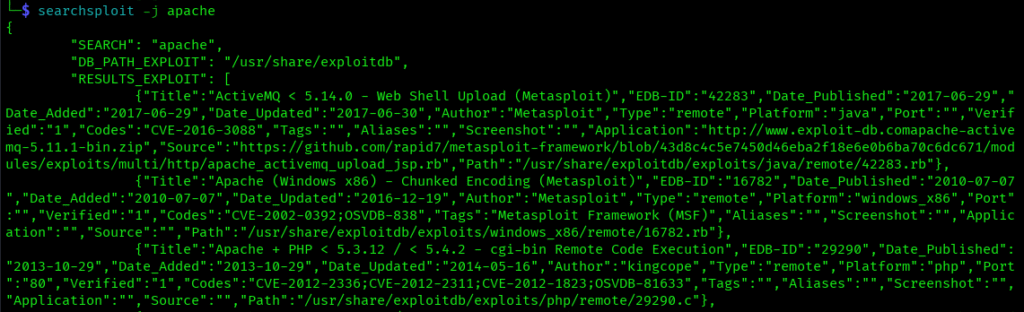
Perfect for automation and integration with other tools or custom scripts.
File Management Commands
Copy Exploit to Current Directory (-m, –mirror [EDB-ID])
Copies the specified exploit to your current directory:
searchsploit -m 46396
or
searchsploit -m exploits/linux/remote/49885.py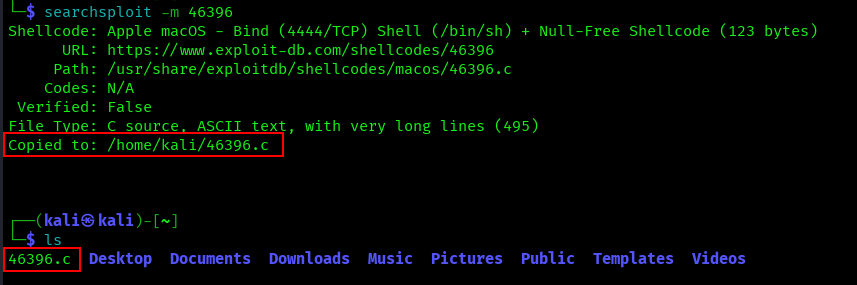
This is your go-to command for actually getting the exploit files you want to work with.
-p, –path
Shows the full file system path to exploits:
searchsploit -p 46396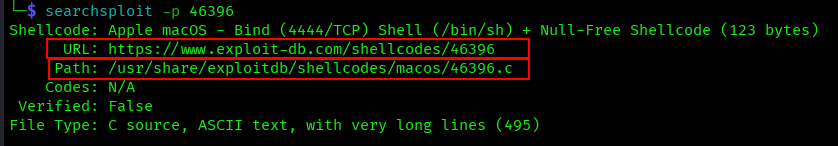
Helpful when you need to know exactly where files are located for scripting or manual access.
-x, –examine [EDB-ID]
Displays the exploit source code directly in your terminal:
searchsploit -x 12345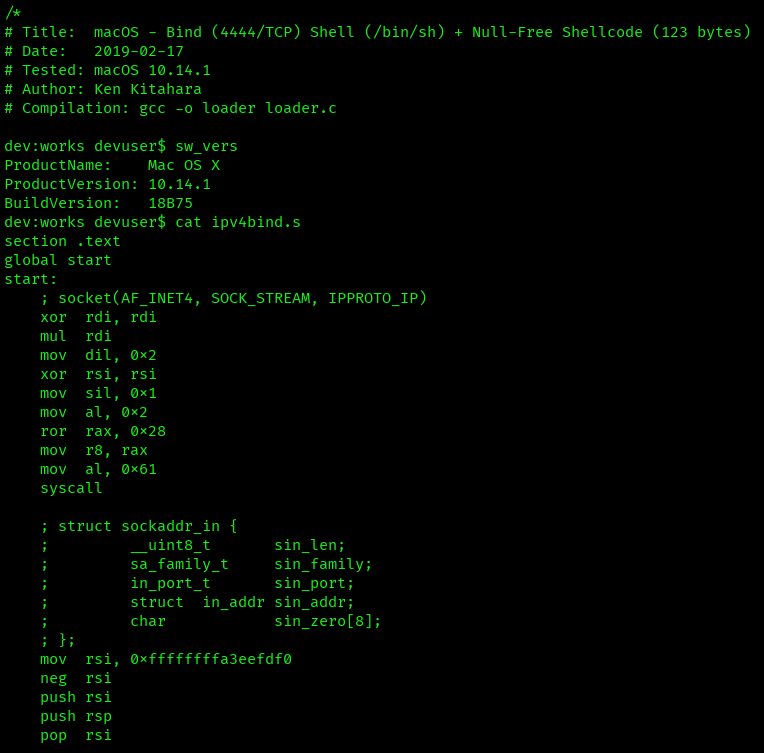
Perfect for quickly reviewing exploit code without opening separate files.
–copy [EDB-ID]
Alternative method to copy exploits to current directory:
searchsploit --copy 12345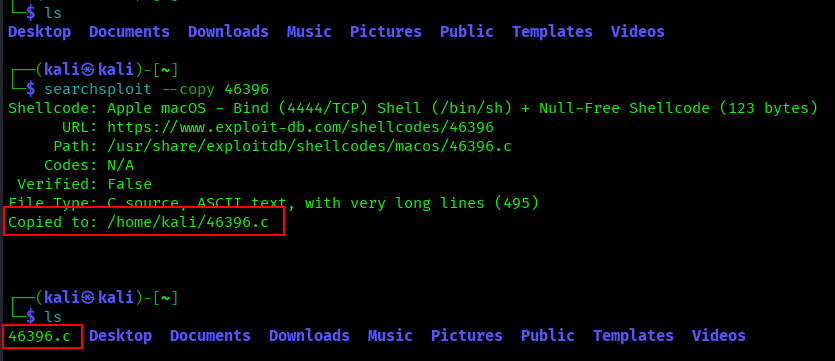
Functions similarly to -m but with slightly different behavior in some edge cases.
Advanced Filtering Options
–exclude [term]
Excludes results containing specific terms:
searchsploit --exclude="dos" apache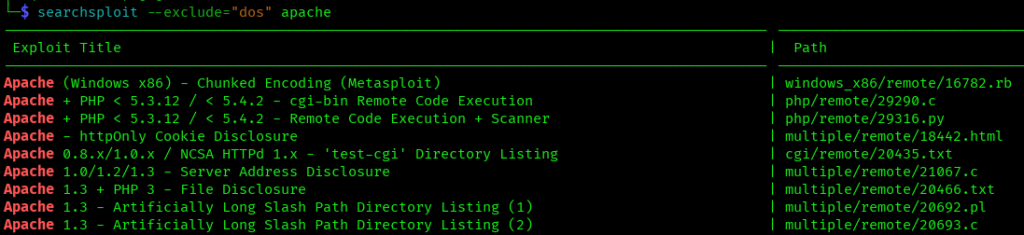
Incredibly useful for filtering out denial-of-service exploits when you need remote code execution.
-o, –overflow
Shows more results by extending the output buffer:
searchsploit -o apacheUse this when you suspect there are more results than what’s being displayed.
Database Management Commands
-u, –update
Updates the local exploit database:
searchsploit -uRun this regularly to ensure you have access to the latest exploits and security research.
-h, –help
Displays all available options and usage information:
$ searchsploit -h
Usage: searchsploit [options] term1 [term2] ... [termN]
==========
Examples
==========
searchsploit afd windows local
searchsploit -t oracle windows
searchsploit -p 39446
searchsploit linux kernel 3.2 --exclude="(PoC)|/dos/"
searchsploit -s Apache Struts 2.0.0
searchsploit linux reverse password
searchsploit -j 55555 | jq
searchsploit --cve 2021-44228
For more examples, see the manual: https://www.exploit-db.com/searchsploit
=========
Options
=========
## Search Terms
-c, --case [term] Perform a case-sensitive search (Default is inSEnsITiVe)
-e, --exact [term] Perform an EXACT & order match on exploit title (Default is an AND match on each term) [Implies "-t"]
e.g. "WordPress 4.1" would not be detect "WordPress Core 4.1")
-s, --strict Perform a strict search, so input values must exist, disabling fuzzy search for version range
e.g. "1.1" would not be detected in "1.0 < 1.3")
-t, --title [term] Search JUST the exploit title (Default is title AND the file's path)
--exclude="term" Remove values from results. By using "|" to separate, you can chain multiple values
e.g. --exclude="term1|term2|term3"
--cve [CVE] Search for Common Vulnerabilities and Exposures (CVE) value
## Output
-j, --json [term] Show result in JSON format
-o, --overflow [term] Exploit titles are allowed to overflow their columns
-p, --path [EDB-ID] Show the full path to an exploit (and also copies the path to the clipboard if possible)
-v, --verbose Display more information in output
-w, --www [term] Show URLs to Exploit-DB.com rather than the local path
--id Display the EDB-ID value rather than local path
--disable-colour Disable colour highlighting in search results
## Non-Searching
-m, --mirror [EDB-ID] Mirror (aka copies) an exploit to the current working directory
-x, --examine [EDB-ID] Examine (aka opens) the exploit using $PAGER
## Non-Searching
-h, --help Show this help screen
-u, --update Check for and install any exploitdb package updates (brew, deb & git)
## Automation
--nmap [file.xml] Checks all results in Nmap's XML output with service version
e.g.: nmap [host] -sV -oX file.xml
=======
Notes
=======
* You can use any number of search terms
* By default, search terms are not case-sensitive, ordering is irrelevant, and will search between version ranges
* Use '-c' if you wish to reduce results by case-sensitive searching
* And/Or '-e' if you wish to filter results by using an exact match
* And/Or '-s' if you wish to look for an exact version match
* Use '-t' to exclude the file's path to filter the search results
* Remove false positives (especially when searching using numbers - i.e. versions)
* When using '--nmap', adding '-v' (verbose), it will search for even more combinations
* When updating or displaying help, search terms will be ignored
Your quick reference when you forget command syntax.
Display Customization Options
–disable-colour
Removes color formatting from output:
searchsploit --disable-colour apache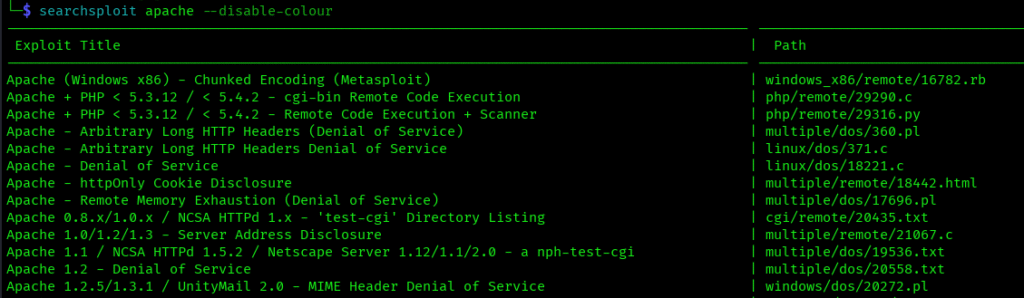
Clean output for logging or when colors interfere with your workflow.
Real-World Application Scenarios
Apache Server Vulnerability Research
When you discover an Apache server during reconnaissance, here’s how you’d systematically search for exploits:
searchsploit apache 2.4.41
searchsploit apache 2.4.49
searchsploit "apache httpd 2.4"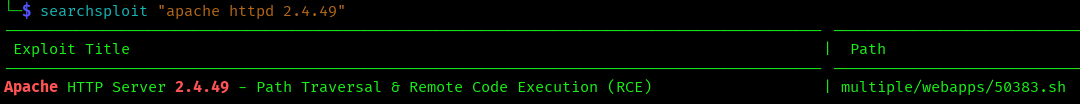
The beauty of SearchSploit is its flexibility with version numbers. You can search for exact versions, partial versions, or even include the full software name for more precision.
CMS and Web Application Hunting
Content management systems are goldmines for vulnerabilities. Here’s how you’d approach different platforms:
searchsploit drupal
searchsploit wordpress 5.8
searchsploit joomla 3.9
searchsploit phpmyadminEach search gives you a different perspective on available exploits, from version-specific vulnerabilities to general platform weaknesses.
Network Service Exploitation Research
Network services often have well-documented exploits. Your approach might look like this:
searchsploit openssh 7.4
searchsploit nginx 1.18.0
searchsploit samba 4.13
searchsploit vsftpd 3.0.5The key is being specific with version numbers when you have them, but don’t be afraid to search more broadly if exact versions don’t yield results.
Integration with Security Testing Tools
SearchSploit and Nmap Workflow
The real magic happens when you combine searchsploit with nmap results. After running your network scan, you can immediately search for exploits based on discovered services:
nmap -sV 192.168.1.100
# Assume Nmap reveals Apache 2.4.41
searchsploit apache 2.4.41
searchsploit -m 47688 # Copy promising exploitSearching with Nmap Results
A powerful combination is using SearchSploit with Nmap. You can feed the XML output from an Nmap scan directly into SearchSploit to automatically find relevant exploits for the discovered services.
Run an Nmap scan with the -oX flag to save the output in XML format.
nmap -sV -oX scan_results.xml <target_ip>Use the searchsploit --nmap command to parse the file.
searchsploit --nmap scan_results.xmlThis will list potential exploits for each service identified by Nmap, streamlining the vulnerability discovery process.
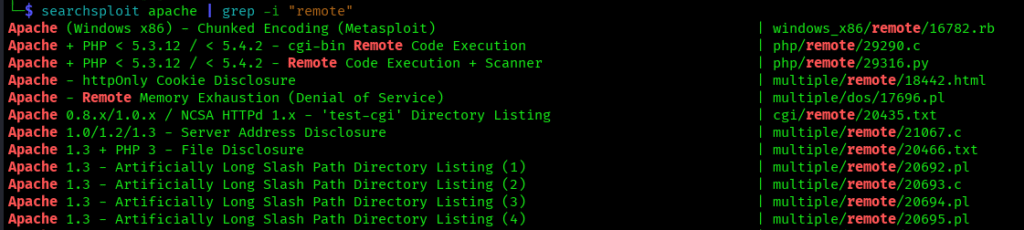
Combine with grep for Filtering
searchsploit apache | grep -i "remote"
This command will Filters results to show only remote exploits for Apache.
Metasploit Framework Integration
While SearchSploit excels at finding exploits, Metasploit provides the framework for execution. Your typical workflow might involve using searchsploit to identify available exploits, then checking if corresponding Metasploit modules exist for easier exploitation.
CVE-Based Vulnerability Research
One of SearchSploit’s most powerful features is CVE integration. When you have vulnerability reports with CVE numbers, you can quickly cross-reference them:
searchsploit --cve 2021-44228
searchsploit cve apache
searchsploit --cve 2017 # Find all 2017 CVEsThis searchsploit search by cve functionality is invaluable when working with vulnerability assessments or compliance reports.
Database Maintenance and Updates
Keeping your exploit database current is crucial. The searchsploit update process is straightforward but important:
searchsploit -uThis command connects to the official repository and downloads the latest exploits. Think of it as subscribing to a daily newsletter, but for security vulnerabilities.
The searchsploit directory kali is typically located at /usr/share/exploitdb/, and understanding this structure helps when you need to browse manually or create automation scripts.
Practical Penetration Testing Workflow
Here’s how SearchSploit fits into a real-world penetration test:
Discovery Phase: You run Nmap scans and identify running services
Research Phase: You use SearchSploit to find relevant exploits for discovered services
Analysis Phase: You examine exploit code using searchsploit -x to understand requirements
Preparation Phase: You copy promising exploits with searchsploit -m for modification
Execution Phase: You adapt and execute the most suitable exploits
OSCP Examination Preparation
If you’re preparing for OSCP, mastering SearchSploit is essential. The tool is allowed during the exam, and having a solid searchsploit cheat sheet with your favorite commands can save precious time. Many successful candidates emphasize the importance of being comfortable with all the major command options.
Troubleshooting Common Issues
Command Not Found Errors
When you get “searchsploit command not found” errors, here’s your troubleshooting checklist:
- Verify installation:
which searchsploit - Check your PATH variable:
echo $PATH - Reinstall the package:
sudo apt install exploitdb - Look for broken symbolic links:
ls -la /usr/bin/searchsploit
Database Update Problems
Sometimes the update searchsploit db process encounters issues:
- Network connectivity problems require checking your internet connection
- Permission issues might need
sudo searchsploit -u - Corrupted database files can be fixed by removing
/usr/share/exploitdb/.gitand updating again
Exploit Execution Challenges
When exploits don’t work as expected, your debugging process should include:
- Reading the exploit code thoroughly with
searchsploit -x EDB-ID - Checking system compatibility and dependencies
- Testing in controlled lab environments first
- Modifying exploit parameters for your specific target
Alternative Tools and Resources
While SearchSploit is fantastic, it’s worth knowing about searchsploit alternatives:
Online Resources:
- Exploit-DB website for web-based searching
- CVE Details for comprehensive vulnerability information
- Packet Storm Security for latest exploit releases
- GitHub repositories with proof-of-concept codes
Complementary CLI Tools:
- Metasploit Framework for exploitation
- Nuclei for vulnerability templating
- Custom CVE lookup utilities
- Various vulnerability scanner integrations
- MSFvenom / AutoSploit
Security and Legal Considerations
SearchSploit gives you access to powerful exploitation tools, but remember that with great power comes great responsibility. Only use these capabilities on systems you own or have explicit authorization to test. Unauthorized access remains illegal regardless of the tools used.
Before executing any exploit:
- Read and understand the code completely
- Test in your own laboratory environment
- Document all activities thoroughly
- Ensure you have proper written authorization
- Have rollback procedures ready
Community and Development
SearchSploit isn’t just a tool – it’s part of a vibrant security community. The searchsploit github repository serves as the development hub where you can:
- Report bugs and suggest improvements
- Contribute newly discovered exploits
- Access bleeding-edge development versions
- Participate in community discussions
The tool continues evolving with regular updates, new features, and improved functionality, all backed by Offensive Security and a global community of security researchers.
Conclusion
SearchSploit has earned its reputation as an indispensable tool for security professionals. Whether you’re conducting penetration tests, preparing for certifications, or diving deep into vulnerability research, mastering SearchSploit gives you immediate access to one of the world’s most comprehensive exploit databases.
The real power of SearchSploit lies not just in its vast database, but in how quickly and efficiently you can find exactly what you need. From basic searches to complex CVE cross-referencing, from simple exploit copying to advanced automation integration – SearchSploit adapts to your workflow.
Remember that becoming proficient with SearchSploit is about more than memorizing commands. It’s about understanding how to efficiently research vulnerabilities, analyze exploit code, and integrate findings into your broader security testing methodology.
Most importantly, always use these powerful capabilities ethically and legally. The cybersecurity community thrives on responsible disclosure, knowledge sharing, and ethical behavior. Use SearchSploit to make systems more secure, never to cause harm.
Whether you’re just starting your security journey or you’re a seasoned professional refining your skills, SearchSploit will be there to help you find the right exploit at the right time. Master it, respect it, and let it enhance your security testing capabilities.







