Network reconnaissance is a critical phase in penetration testing and security auditing. While tools like Nmap dominate the scanning landscape, netdiscover offers a specialized approach to network discovery through ARP reconnaissance. This comprehensive guide covers everything security professionals need to know about netdiscover tool/command, from basic usage to advanced techniques.
What is Netdiscover?
Netdiscover tool is an active/passive ARP reconnaissance tool designed for network discovery without relying on DHCP servers. Originally developed for wireless network discovery during wardriving activities, it has evolved into a versatile network inventory tool used by penetration testers and security analysts worldwide.
Unlike traditional IP scanners that rely on ICMP or TCP/UDP probes, netdiscover operates at the data link layer using ARP requests. This approach makes it particularly effective in switched network environments where broadcast traffic is contained within VLANs.
Key Features
- ARP-based discovery: Uses Address Resolution Protocol for host detection
- Passive and Active scanning modes: Flexibility in reconnaissance approach
- No DHCP dependency: Works effectively in DHCP-less networks
- Vendor identification: Automatic OUI lookup for device fingerprinting
- Lightweight and fast: Minimal resource consumption
- Cross-platform support: Available for Linux, macOS, and Windows
How Netdiscover Works
Understanding the underlying mechanism helps security professionals leverage netdiscover effectively. The tool functions by sending ARP requests to target IP addresses and analyzing the responses to build a network map.
ARP Reconnaissance Process
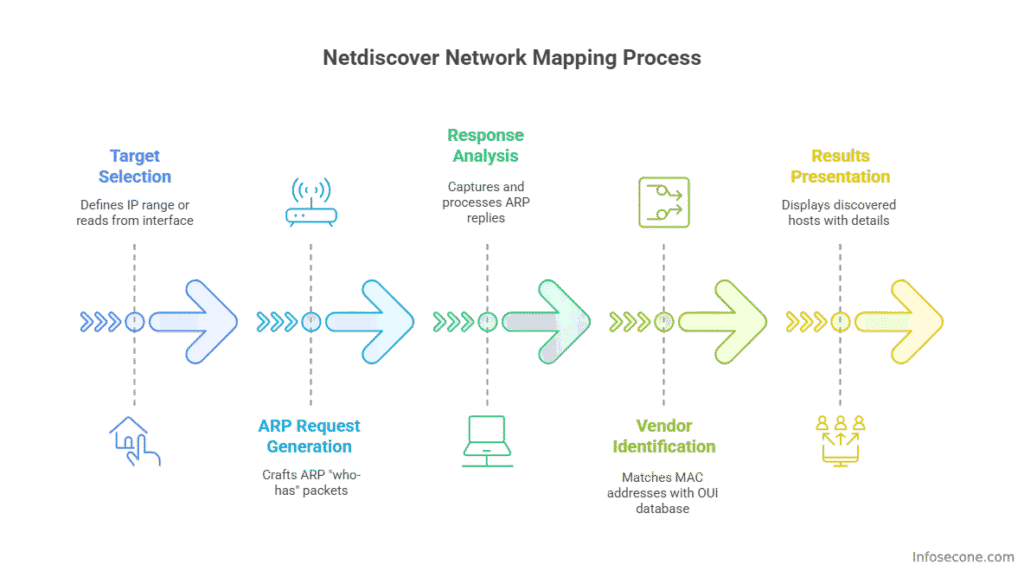
- Target Selection: Defines IP range or reads from interface
- ARP Request Generation: Crafts ARP “who-has” packets
- Response Analysis: Captures and processes ARP replies
- Vendor Identification: Matches MAC addresses with OUI database
- Results Presentation: Displays discovered hosts with details
In passive mode, netdiscover monitors existing ARP traffic without generating additional network noise, making it ideal for stealth reconnaissance.
Installation Guide
Kali Linux
Netdiscover command comes pre-installed on Kali Linux. If missing, install using:
sudo apt update
sudo apt install netdiscoverUbuntu and Debian
sudo apt update
sudo apt install netdiscoverFedora and RHEL
sudo dnf install netdiscoverArch Linux
sudo pacman -S netdiscovermacOS
Using Homebrew:
brew install netdiscoverWindows
While netdiscover doesn’t have native Windows support, you can use:
- Windows Subsystem for Linux (WSL)
- Virtual machines with Linux
- Docker containers
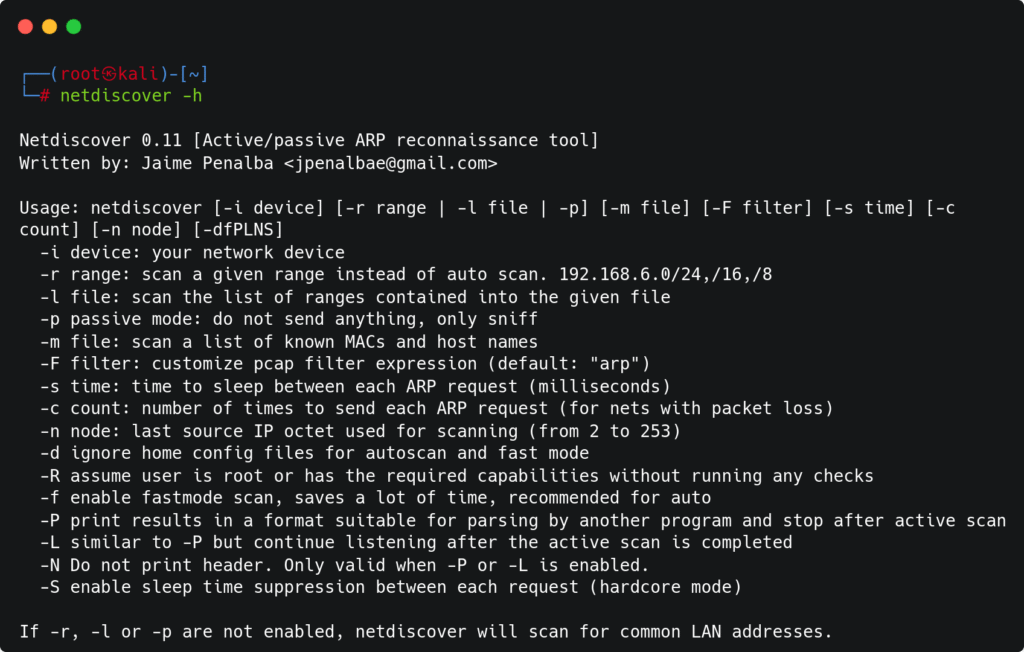
Command Line Options and Parameters
Netdiscover’s power lies in its flexible command-line interface. Let’s explore each option systematically.
Basic Syntax
netdiscover [options] Range Scanning (-r)
The most commonly used option for specifying target networks. You can specify multiple ranges separated by commas:
netdiscover -r 192.168.1.0/24
netdiscover -r 10.0.0.0/8
netdiscover -r 192.168.1.0/24,10.0.0.0/16Sample Terminal Output:
$ sudo netdiscover -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
This discovers all active hosts in the typical home/office network range.
Use Cases:
- Internal network reconnaissance
- Subnet discovery
- Network inventory
Interface Selection (-i)
Please select the network interface you wish to utilize. This step is frequently necessary, particularly on systems with multiple network connections(like WIFI router, ethernet/lan cable connection, VPN connection, docker-container network, etc).
netdiscover -i eth0 -r 192.168.1.0/24
netdiscover -i wlan0 -r 10.0.0.0/24
netdiscover -i tun0 -r 192.168.100.0/24Sample Terminal Output:
$ sudo netdiscover -i wlan0 -r 192.168.43.0/24
Currently scanning: 192.168.43.0/24 | Screen View: Unique Hosts
5 Captured ARP Req/Rep packets, from 4 hosts. Total size: 300
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.43.1 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
192.168.43.108 aa:bb:cc:11:22:33 2 60 Apple, Inc.
192.168.43.200 ff:ee:dd:44:55:66 1 60 Xiaomi Communications Co Ltd
192.168.43.250 00:11:22:33:44:55 1 60 Unknown vendor
Critical for:
- Multi-homed/multi-interface systems
- VPN assessments
- Wireless penetration testing
Passive Mode (-p)
For Stealth Reconnaissance, use Netdiscover passive mode
Enable passive ARP monitoring. Netdiscover will only listen for ARP traffic without sending requests. This is the default if -r or -l are not used:
netdiscover -p -i eth0Sample Terminal Output:
$ sudo netdiscover -p -i eth0
Currently scanning: (passive) | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 5 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 2 60 Dell Inc.
192.168.1.50 08:00:27:a1:b2:c3 1 60 PCS Systemtechnik GmbH
192.168.1.75 aa:bb:cc:dd:ee:ff 3 60 Apple, Inc.
192.168.1.100 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
192.168.1.200 ff:ee:dd:cc:bb:aa 1 60 Unknown vendor
Monitor network traffic without generating suspicious ARP requests.
Benefits:
- Stealth reconnaissance
- Network traffic analysis
- Compliance with engagement rules
Print/Parsable Output (-P)
Print results in a format suitable for parsing by another program and stop after the active scan:
netdiscover -P -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -P -r 192.168.1.0/24
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Generate machine-readable output for scripts. Perfect for integration with other security tools and automated reporting.
Applications:
- Script integration
- Automated reporting
- Data processing pipelines
Advanced Options
Count Specification (-c)
Set the number of times to send each ARP request. This can be useful on networks with packet loss:
netdiscover -c 5 -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -c 5 -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
12 Captured ARP Req/Rep packets, from 3 hosts. Total size: 720
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 5 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 4 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 3 60 Unknown vendor
This sends exactly 5 ARP requests per target, useful for:
- Time-constrained assessments
- Networks with packet loss
- Increasing detection reliability
Fast Mode (-f)
Enable fast mode scan. This saves time and is recommended for automatic scans:
netdiscover -f -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -f -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
-- Ending netdiscover at: Fri Jun 20 14:23:15 2025 -- 3 hosts found.
Quick scan with limited requests per host.
Trade-offs:
- Faster completion time
- Potential for missed hosts
- Higher network load
Filter Configuration (-F)
Customize the pcap filter expression. The default filter is "arp":
netdiscover -F "arp and src net 192.168.1.0/24" -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -F "arp and src net 192.168.1.0/24" -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
2 Captured ARP Req/Rep packets, from 2 hosts. Total size: 120
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.200 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
List/File Input (-l)
Scan the IP address ranges listed in the given file. Each range should be on a separate line:
netdiscover -l targets.txtFile format example (targets.txt):
192.168.1.0/24
10.0.0.1-10.0.0.50
172.16.1.1Sample Terminal Output:
$ sudo netdiscover -l targets.txt
Currently scanning: File | Screen View: Unique Hosts
6 Captured ARP Req/Rep packets, from 5 hosts. Total size: 360
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
10.0.0.10 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
10.0.0.25 ff:ee:dd:cc:bb:aa 2 60 Apple, Inc.
172.16.1.1 aa:bb:cc:11:22:33 1 60 Cisco Systems, Inc
MAC/Hostname File (-m)
Scan a list of known MAC addresses and hostnames from the given file. This allows you to associate known names with discovered MAC addresses:
netdiscover -m known_hosts.txt -r 192.168.1.0/24File format example (known_hosts.txt):
00:14:22:01:23:45 server01
08:00:27:53:81:2b workstation-lab
aa:bb:cc:dd:ee:ff printer-hpSample Terminal Output:
$ sudo netdiscover -m known_hosts.txt -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc. / server01
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH / workstation-lab
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor / printer-hp
Enhanced information:
- Physical address identification
- Hostname correlation
- Asset management integration
Sleep Time (-s)
Set the sleep time (in milliseconds) between each ARP request (used with active scanning):
netdiscover -s 100 -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -s 100 -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Use cases:
- Rate limiting for stealth
- Network congestion management
- IDS evasion
Sleep Suppression (-S)
Enable sleep time suppression between each request (hardcore mode). Use with extreme caution as it can flood the network:
netdiscover -S -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -S -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
-- Ending netdiscover at: Fri Jun 20 14:25:32 2025 -- 3 hosts found.
Caution: May trigger intrusion detection systems and flood the network.
Node Specification (-n)
Set the last source IP octet used for scanning (from 2 to 253). This can be useful for avoiding conflicts or specific IP ranges:
netdiscover -n 100 -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -n 100 -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.50 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Continuous Listening (-L)
Similar to -P, but continues listening after the active scan is completed:
netdiscover -L -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -L -r 192.168.1.0/24
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
192.168.1.200 ff:ee:dd:cc:bb:aa 1 60 Apple, Inc.
192.168.1.150 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
No Header (-N)
Do not print the header. Only valid when -P or -L is enabled:
netdiscover -P -N -r 192.168.1.0/24
Sample Terminal Output:
$ sudo netdiscover -P -N -r 192.168.1.0/24
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Ignore Home Configuration (-d)
Ignore home configuration files for autoscan and fast mode:
netdiscover -d -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -d -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Practical Usage Examples
Wireless Network Discovery
For wireless assessments:
sudo netdiscover -i wlan0 -r 192.168.43.0/24Sample Terminal Output:
$ sudo netdiscover -i wlan0 -r 192.168.43.0/24
Currently scanning: 192.168.43.0/24 | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 5 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.43.1 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
192.168.43.108 aa:bb:cc:11:22:33 2 60 Apple, Inc.
192.168.43.150 ff:ee:dd:44:55:66 1 60 Xiaomi Communications Co Ltd
192.168.43.200 00:11:22:33:44:55 2 60 Huawei Technologies Co.,Ltd
192.168.43.250 bb:aa:cc:dd:ee:ff 2 60 Unknown vendor
Common for mobile hotspot and wireless AP reconnaissance.
VPN Tunnel Scanning
During VPN assessments:
sudo netdiscover -i tun0 -r 10.8.0.0/24Sample Terminal Output:
$ sudo netdiscover -i tun0 -r 10.8.0.0/24
Currently scanning: 10.8.0.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 2 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
10.8.0.1 00:ff:12:34:56:78 1 60 OpenVPN Technologies, Inc.
10.8.0.100 aa:bb:cc:dd:ee:ff 2 60 Unknown vendor
Discover hosts accessible through VPN connections.
Understanding Output
Netdiscover provides structured output containing:
Standard Output Format
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 3 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:11:22:33:44:55 1 60 Router Manufacturer Inc.
192.168.1.100 aa:bb:cc:dd:ee:ff 2 60 Dell Inc.
192.168.1.200 ff:ee:dd:cc:bb:aa 1 60 Apple, Inc.
Output Components
- IP Address: Target host IP
- MAC Address: Physical network interface identifier
- Count: Number of ARP responses received
- Len: Packet length in bytes
- Vendor: Manufacturer identification from OUI database
Troubleshooting Common Issues
“Command Not Found” Error
Problem: bash: netdiscover: command not found
Sample Terminal Output:
$ netdiscover -r 192.168.1.0/24
bash: netdiscover: command not found
Solutions:
- Install netdiscover:
sudo apt install netdiscover - Check PATH:
which netdiscover - Use full path:
/usr/bin/netdiscover
Permission Denied
Problem: You must be root to run this
Sample Terminal Output:
$ netdiscover -r 192.168.1.0/24
You must be root to run this. (Maybe install pcap dev?. I use libpcap's pcap_open_live method)
Solution: Use sudo privileges:
sudo netdiscover -r 192.168.1.0/24“Not an Ethernet Interface” Error
Problem: Interface specification issues
Sample Terminal Output:
$ sudo netdiscover -i wlan1 -r 192.168.1.0/24
Fatal: wlan1 is not an ethernet interface. I use libnet's libnet_build_arp method.
Solutions:
- List interfaces:
ip link show - Verify interface name:
netdiscover -i wlan0 - Check interface status:
ip link show wlan0
No Results Found
Problem: Netdiscover doesn’t find anything
Sample Terminal Output:
$ sudo netdiscover -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
0 Captured ARP Req/Rep packets, from 0 hosts. Total size: 0
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
-- Ending netdiscover at: Fri Jun 20 14:35:12 2025 -- 0 hosts found.
Troubleshooting steps:
- Verify network connectivity
- Check firewall rules
- Confirm target range
- Try different interface
- Use passive mode for monitoring
Alternative approach with passive mode:
sudo netdiscover -p -i eth0Package Installation Issues
Problem: unable to locate package netdiscover
Sample Terminal Output:
$ sudo apt install netdiscover
Reading package lists... Done
Building dependency tree
Reading state information... Done
E: Unable to locate package netdiscover
Solutions:
- Update package lists:
sudo apt update - Install from source: Download from GitHub repository
- Use alternative package manager:
sudo snap install netdiscover
Netdiscover vs Other Tools
Netdiscover vs Nmap
| Feature | Netdiscover | Nmap |
|---|---|---|
| Protocol | ARP only | TCP/UDP/ICMP |
| Speed | Fast for local networks | Comprehensive but slower |
| Stealth | Excellent passive mode | Various stealth techniques |
| Functionality | Network discovery focused | Full-featured scanner |
| Learning curve | Simple | Complex |
Netdiscover vs ARP-scan
Netdiscover advantages:
- Better passive monitoring
- Integrated vendor lookup
- Wireless network focus
ARP-scan advantages:
- More customization options
- Better scripting support
- Advanced filtering
Alternative Tools
For Windows environments:
- Angry IP Scanner
- Advanced IP Scanner
- Fing
For comprehensive scanning:
- Nmap with ARP scan (-sn)
- Masscan for large networks
- Zmap for internet-wide scanning
Advanced Techniques
Script Integration
Combine netdiscover with other tools for comprehensive reconnaissance:
#!/bin/bash
# Network discovery pipeline
netdiscover -P -r $1 | grep -E "^[0-9]" | cut -d' ' -f1 > discovered_hosts.txt
nmap -sV -iL discovered_hosts.txt
Sample execution and output:
$ ./network_recon.sh 192.168.1.0/24
$ cat discovered_hosts.txt
192.168.1.1
192.168.1.100
192.168.1.254
Starting Nmap 7.80 ( https://nmap.org ) at 2025-06-20 14:40 EDT
Nmap scan report for 192.168.1.1
Host is up (0.001s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3
Automated Reporting
Generate structured reports for documentation:
netdiscover -P -r 192.168.1.0/24 | \
awk '/^[0-9]/ {print $1","$2","$6}' > network_inventory.csvSample CSV output:
$ cat network_inventory.csv
192.168.1.1,00:14:22:01:23:45,Dell Inc.
192.168.1.100,08:00:27:53:81:2b,PCS Systemtechnik GmbH
192.168.1.254,aa:bb:cc:dd:ee:ff,Unknown vendor
Continuous Monitoring
Set up continuous network monitoring for security purposes:
#!/bin/bash
# Continuous monitoring script
LOG_FILE="/var/log/netdiscover_monitor.log"
while true; do
echo "$(date): Starting network scan" >> $LOG_FILE
netdiscover -P -c 3 -r 192.168.1.0/24 >> $LOG_FILE 2>&1
echo "$(date): Scan completed" >> $LOG_FILE
sleep 300
done
Sample log output:
$ tail -f /var/log/netdiscover_monitor.log
Fri Jun 20 14:45:01 EDT 2025: Starting network scan
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
Fri Jun 20 14:45:15 EDT 2025: Scan completed
Multi-Range Scanning
Scan multiple network ranges efficiently:
#!/bin/bash
# Multi-range scanner
RANGES="192.168.1.0/24,10.0.0.0/24,172.16.1.0/24"
netdiscover -P -r $RANGES
Sample Terminal Output:
$ sudo netdiscover -P -r 192.168.1.0/24,10.0.0.0/24,172.16.1.0/24
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
10.0.0.1 12:34:56:78:9a:bc 1 60 Samsung Electronics Co.,Ltd
10.0.0.50 ff:ee:dd:cc:bb:aa 1 60 Apple, Inc.
172.16.1.1 aa:bb:cc:11:22:33 1 60 Cisco Systems, Inc
Custom Filter Implementation
Create advanced filtering for specific reconnaissance needs:
# Filter for specific vendor equipment
netdiscover -P -r 192.168.1.0/24 | grep -i "cisco\|dell\|hp"Sample filtered output:
$ sudo netdiscover -P -r 192.168.1.0/24 | grep -i "cisco\|dell\|hp"
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.50 00:1b:21:3c:4d:5e 1 60 Cisco Systems, Inc
192.168.1.200 3c:d9:2b:12:34:56 1 60 Hewlett Packard
Stealth Scanning with Custom Timing
Implement stealth techniques to avoid detection:
# Ultra-stealth scan with random delays
sudo netdiscover -s 5000 -c 1 -r 192.168.1.0/24Sample Terminal Output:
$ sudo netdiscover -s 5000 -c 1 -r 192.168.1.0/24
Currently scanning: 192.168.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 00:14:22:01:23:45 1 60 Dell Inc.
192.168.1.100 08:00:27:53:81:2b 1 60 PCS Systemtechnik GmbH
192.168.1.254 aa:bb:cc:dd:ee:ff 1 60 Unknown vendor
-- Ending netdiscover at: Fri Jun 20 15:02:33 EDT 2025 -- 3 hosts found.
The scan takes significantly longer but generates minimal network noise.
Legal and Ethical Usage (Security Considerations)
Authorized testing only:
- Obtain written permission
- Follow engagement rules
- Document activities and collect scanning logs
- Report findings responsibly
Integration with Penetration Testing
Reconnaissance Phase
Netdiscover fits early in the kill chain:
- Passive reconnaissance: Gather public information
- Active reconnaissance: Netdiscover for host discovery
- Enumeration: Detailed service scanning
- Vulnerability assessment: Identify weaknesses
Conclusion
Netdiscover remains an essential tool for network reconnaissance, particularly in environments where traditional scanning methods fall short. Its ARP-based approach provides unique advantages for discovering hosts in switched networks and wireless environments.
The tool’s simplicity shouldn’t be underestimated – often the most effective reconnaissance comes from understanding when to use specialized tools like netdiscover rather than relying solely on comprehensive scanners like Nmap.
For security professionals, mastering netdiscover’s various modes and options provides another valuable technique in the network discovery arsenal. Whether conducting authorized penetration tests, performing network inventories, or investigating security incidents, netdiscover’s focused functionality delivers reliable results.
Remember that effective network reconnaissance combines multiple tools and techniques. Netdiscover excels at its specific function – use it as part of a comprehensive methodology rather than a standalone solution.
Additional Resources
- Official documentation: Man page (
man netdiscover) - Source code: Available on Netdiscover GitHub repository
- Community forums: Security-focused discussion groups
- Training courses: Penetration testing certification programs
- Related tools: Explore the broader network reconnaissance toolkit
This guide provides a foundation for using netdiscover effectively. Practice in authorized environments, stay current with updates, and always operate within legal and ethical boundaries.







